Internet packages energy our on-line revel in day in and day trip. We attach, have interaction, store, and watch humorous cat movies – all the usage of internet apps. They ship important enterprise products and services and cling delicate knowledge, however the extra we use one thing, the extra vulnerable it turns into to attacks.
One cyberattack to be careful for on apps that exploit vulnerabilities in structured question language (SQL) is the typical and perilous SQL injection.
What’s SQL injection?
SQL injection (SQLi) is a damaging code injection methodology cyber attackers use to take advantage of vulnerabilities in internet packages. They leverage the susceptible spots to realize unauthorized get entry to by way of including a string of malicious code to a database question.
SQL injection assaults result in unsuitable knowledge get entry to, manipulation, identification robbery, monetary loss, popularity injury, and criminal penalties. Builders and organizations have to know its dangers and put in force complete security features. Equipment like internet software firewalls (WAF) instrument and virtual forensics instrument are designed to protect in opposition to SQL injection assaults. Companies too can rely on complete site safety suites to offer protection to their apps.
Learn this SQL injection cheat sheet to understand how SQL assaults are done with examples, their diversifications, and how one can save you such assaults.
Why are SQL injection assaults unhealthy?
SQL injection has been within the Open International Software Safety Mission’s (OWASP) best 10 record of internet software safety dangers for years. In 2022 on my own, OWASP discovered 274,000+ occurrences of a few type of injection within the apps they examined; SQL injection and cross-site scripting (XSS) have been the most typical.
Attackers can use SQl injections to purpose:
- Mistakes in internet packages by way of enhancing or deleting knowledge inside of a database.
- Information breaches if hackers get unauthorized get entry to to delicate knowledge saved in databases, equivalent to non-public knowledge, monetary information, or passwords.
- Compromised techniques by way of getting access to further, unauthorized techniques that use the similar shared databases. This permits attackers to escalate their moves to different techniques at the similar community or carry out allotted denial-of-service (DDoS).
Those harmful movements irrevocably injury companies. The offenses compromise privateness and knowledge integrity, resulting in a lack of buyer agree with and enterprise popularity. It additionally provides a monetary burden to the corporate coping with the aftermath.
Actual-life SQL injection assault examples
It’s been greater than 20 years since SQL injection first got here at the scene. Two decades later, it stays infamous, as evidenced by way of the next outstanding SQL injection incidents.
- Heartland Bills Methods: In 2008, Heartland Bills Methods suffered what used to be one of the most largest knowledge breaches in historical past, exposing over 130 million credit score and debit card main points via an SQLi assault. Heartland paid thousands and thousands in fines.
- Yahoo: In 2012, an SQL injection assault compromised just about 5 million Yahoo customers’ account main points, together with electronic mail addresses and passwords.
- Freepik: Hackers stole the emails and passwords of 8.3 million Freepik and Flaticon customers in 2020 right through an SQL injection assault in opposition to the corporate’s Flaticon site.
- WooCommerce: The preferred WordPress plugin fastened an SQL injection vulnerability that revealed 5 million websites to knowledge robbery.
- BillQuick: Cybercriminals exploited a blind SQL vulnerability in the preferred billing platform to unfold ransomware.
- MOVEit: In Might 2023, the Cl0p ransomware gang used a SQL injection vulnerability within the controlled document switch instrument device MOVEit, affecting over 1,000 organizations and a minimum of 60 million people, making it the biggest knowledge breach within the yr to this point.
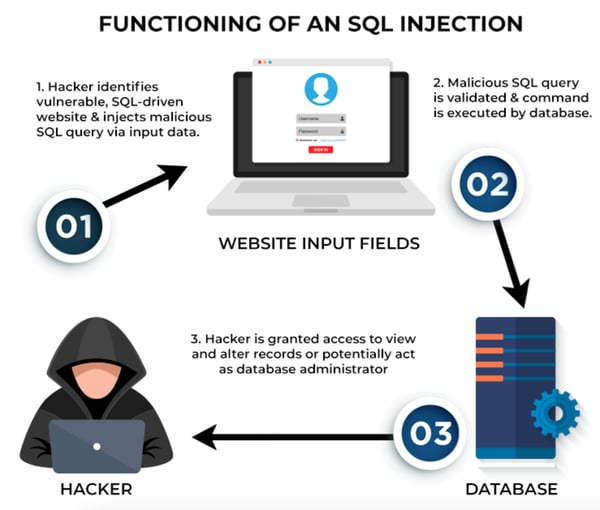
How does an SQL injection assault paintings?
Let’s have a look at the fundamentals of databases and SQL queries we use in trendy internet packages. This may occasionally assist us perceive the interior workings of SQL injection higher.
All internet sites use relational databases, often known as SQL databases, to retailer knowledge about their customers and apps. It may well be person data, login credentials, cost knowledge, or anything concerning the corporate. Take an e-commerce site, as an example. It retail outlets product knowledge, person accounts, order knowledge, and cost knowledge in its database.
The internet sites then take the information from those databases and ship content material or products and services particular to the customers. This procedure occurs due to SQL, a standardized programming language used for managing databases. On every occasion you wish to have to get one thing from an app, say your acquire historical past, you’re, in reality, creating a request to the database the usage of SQL queries, a command that instructs a database to accomplish a selected motion.
In an try to make internet interactions seamless, many internet sites let customers input knowledge to make SQL queries. This will come with such things as seek phrases, usernames, or cost main points.
Imagine the e-commerce site’s instance. A easy SQL question to show your order historical past from the database with “orders” desk (o) and a “merchandise” desk (p) can be as follows:
SELECT o.order_id, o.order_date, p.product_name, p.value
FROM orders o
JOIN merchandise p ON o.product_id = p.product_id
WHERE o.user_id = 12345;
This SQL code alternatives the order ID and date from the orders desk, together with the product title and value from the product desk for USER ID 12345 from the site database. Usually, the ID can be in keeping with enter from the person. Issues rise up when the enter isn’t correctly checked and regulated. Attackers exploit this vulnerability to hold out an SQL injection assault.
This is the way it normally unfolds.
SQL injection instance
Imagine a internet software that makes use of a URL parameter to fetch product main points in keeping with a product ID, like this:
http://instance.com/merchandise?identity=1
An attacker would possibly attempt to inject malicious SQL code to purpose an error and retrieve knowledge like this: http://instance.com/merchandise?identity=1′ OR 1=1; –
If the appliance fails to validate and sanitize person enter adequately, the SQL question may well be manipulated as follows:
SELECT * FROM merchandise WHERE identity = ‘1’ OR 1=1; – – ‘;
On this case, the unique question used to be designed to retrieve a product with ID 1, however the attacker’s enter modifies the question to go back all merchandise as a result of the addition of 1=1 and the appended double hyphen (- -). It nullifies the unique remaining unmarried quote and ends up in penalties showing all product main points or revealing error messages that attackers can exploit.
33%
of internet software serious vulnerabilities in 2022 have been because of SQL injections.
Supply: Statista
The well-liked incidence of SQL vulnerabilities and the appeal of the internet app database with all its business-critical knowledge makes SQL injection one of the vital power cyberattacks.
 Supply: Spiceworks
Supply: Spiceworks
Sorts of SQL injection assaults
There are 3 primary varieties of SQL injection assaults in keeping with how attackers retrieve knowledge or have interaction with the database:
- Vintage or in-band SQLi
- Blind or inferential SQLi
- Out-of-the-band SQLi
1. Vintage or in-band SQLi
In-band is the most typical form of SQL injection assault. The vintage hacker makes use of the similar communique channel (in-band) to inject malicious SQL code and retrieve the effects. The 2 primary diversifications of in-band SQLi are:
Union-based in-band SQLi
This assault leverages the UNION SQL operator, used to mix knowledge from the results of two or extra SELECT statements. Via doing this, attackers can retrieve knowledge from tables they do not have direct get entry to to.
Error-based in-band SQLi
On this methodology, an attacker deliberately triggers mistakes in an SQL question to take advantage of the mistake messages returned by way of the database. The mistakes can divulge treasured details about the database construction, desk names, column names, and occasionally the information itself. Error-based SQLi will also be done as out-of-the-band SQLi.
2. Inferential (blind) SQLi
In a blind SQLi, the attacker can not without delay see the result of their attack. As an alternative, they infer knowledge by way of watching software habits or error messages that reply to their queries. This sort of assault is time-intensive as hackers must make a sequence of SQL queries to search out attainable vulnerabilities to take advantage of. Two diversifications of blind SQLi are:
Time-based blind SQLi
Right here, the attackers ask queries that make the database prolong its reaction sooner than it reacts. They infer details about the database by way of taking note of reaction time.
Boolean blind SQLi
For Boolean blind SQLi, attackers profit from the best way an software responds to true or false stipulations in SQL queries. Primarily based on the internet software’s responses, they infer details about the database, although no knowledge from the database is returned.
3. Out-of-the-band SQLi
An out-of-the-band SQLi assault reasons the appliance to ship knowledge to a far flung endpoint managed by way of the hackers. An assault like this calls for the SQL servers to have sure options, like with the ability to start up exterior community requests like Hypertext Switch Protocol (HTTP) requests.
Tips on how to save you SQL injection assaults: a cheat sheet
Fighting SQL injection calls for a multi-layered method involving protected coding observe and steady tracking. Here is a cheat sheet with crucial steps to assist stay you protected from SQL injection assaults.
Use ready statements
The principle protection in opposition to SQL injection assaults is ready statements with parameterized queries. Ready statements be certain that person inputs are handled as knowledge relatively than executable code.
Builders collect SQL codes for queries prematurely as templates with placeholders for enter values from the person. On the question execution time, the ready statements bind exact values as a substitute of placeholders. This stops malicious code execution.
Ready statements are preferred over dynamic SQL statements. They write SQL queries right through the execution time, which weakens them in opposition to injection assaults.
Ready statements in common programming languages:
Listed here are language-specific suggestions for the usage of ready statements (parameterized queries) in common database programming:
- Java endeavor version (EE): Use PreparedStatement elegance from the java.sql bundle. Bind parameters the usage of strategies like setString, setInt, and so forth.
- Python (SQLite3): Use placeholders (?) in queries. Bind parameters the usage of a tuple or record.
- PHP: Use the PHP knowledge gadgets (PDO) extension. Make the most of ready statements with placeholders (:). Bind parameters with bindValue or bindParam.
- .NET: Use MySqlCommand object. Bind parameters the usage of Parameters.AddWithValue.
Some other SQL injection prevention means is the usage of saved procedures or a gaggle of pre-compiled SQL codes that can be utilized over and over.
Follow enter validation
Enter validation comes to checking person enter to verify it meets particular standards sooner than processing. An allow-list, often referred to as a white record, is a key facet of enter validation. Right here, best predefined, protected values or patterns are permitted as a part of SQL queries. Any enter that does not fit the set standards is rejected. This actively prevents malignant or surprising enter from coming into the device.
Use object-relational mapping libraries
Object-relational mapping (ORM) libraries are treasured gear for builders running with relational databases. They let builders have interaction with databases the usage of the programming language in their selection, and thereby lowering the will for writing uncooked SQL queries. ORM libraries supply integrated coverage in opposition to SQL injection assaults.
Teach the builders and IT groups on protected coding practices. Be sure you do common safety audits and penetration checking out to search out vulnerabilities.
Put in force the least privilege theory
The least privilege theory best offers database customers the minimal permission required to do their jobs. Following this theory reduces the have an effect on of attainable SQL injection assaults, or any cyberattack, for that topic. Additionally, observe strict get entry to keep an eye on for your database.
Deploy a internet software firewall (WAF)
A WAF displays incoming community site visitors of packages and blocks attainable malicious site visitors in keeping with an inventory of well known assault signatures.
A WAF employs predefined laws to hit upon suspicious patterns and anomalies in incoming site visitors, like SQL key phrases and malicious payloads. It sanitizes and validates person inputs and blocks or filters out destructive requests. This is helping prevent unhealthy SQL queries as they input the device.
Fashionable WAFs adapt to new assault strategies the usage of gadget studying.
Different safety gear to forestall SQL injection assault
Along with WAF, a number of different safety platforms hinder SQL injection assaults.
Guard your knowledge fortresses
SQL injection assaults pose a grave risk to internet app safety. Firms possibility shedding treasured knowledge, person privateness, and their excellent reputations if the assaults prevail.
Whilst no unmarried answer promises absolute protection in opposition to SQL injection, combining the preventive measures we mentioned right here considerably reduces the danger of assaults. Internet builders and database directors must make use of stringent defenses and reinforce their internet apps in opposition to attainable exploitation.
Need a complete approach to protected your site? Discover internet safety instrument and the way it is helping in opposition to cyber assaults that ends up in knowledge breaches.


